-
Rising attack rate is putting business continuity at risk
The attack surface, though shrinking in 2024, remains vast and ever-changing, as IT environments are elastic and expand or shrink based on business demands, highlighting the vulnerability of organizations with inflexible security architectures.
-
Amidst IT cost-cutting, security spending remains a top priority
Despite budget constraints, organizations continue to prioritize cybersecurity investments. According to the 2024 study, security budgets as a portion of IT budgets have increased year over year for organizations of all sizes and across industries.
-
Why zero-trust security must include detection and response
There’s steady growth in the adoption of many security technologies supporting zero-trust network access, such as identity and access management and multifactor authentication. But adoption has declined for threat detection and response technologies.
-
Cybersecurity concerns are hampering cloud adoption
Cloud environments have become the most frequently attacked IT components, and the gap between cloud adoption and cloud security investment has manifested into a top cyber risk for many Canadian organizations.
-
AI and ML are invaluable tools in the modern security landscape
AI and ML are crucial in cybersecurity implementations, thanks to their ability to rapidly analyze vast amounts of data, identify patterns and predict future threats.
-
How to combat adversarial AI with AI strategy
AI can be a double-edged sword in cybersecurity. While AI could empower the adversaries, AI can also be used by cybersecurity teams to help in real-time threat detection and response, automating the process of identifying and neutralizing threats.
-
Recommendations and calls to action
Four recommendations based on the report that can help Canadian organizations strengthen their defences.
April 29, 2024
Cybersecurity in Focus 2024: Top Priorities for Canadian Organizations
Our 2024 Canadian Cybersecurity Study highlights the current state of IT security and key issues facing Canadian businesses and offers insights on how to proactively respond to today’s evolving threat environment.

Cyberattacks are becoming increasingly sophisticated, effective and destructive. As Canadian business and IT leaders seek to protect their data and ensure business continuity, cybersecurity continues to be a top priority. Canadian organizations that adopt AI and machine learning technologies as part of a comprehensive cybersecurity strategy are better equipped to detect and respond to cyberattacks while addressing talent shortages and budget constraints.
Our 2024 Canadian Cybersecurity Study highlights the current state of IT security and key issues facing Canadian businesses and offers insights on how to proactively respond to today’s evolving threat environment.
Rising attack rate is putting business continuity at risk
The IT attack surface is vast and ever-changing
The attack surface of Canadian organizations is vast and encompasses SaaS applications, APIs, containers, VMs, storage systems, database appliances, network appliances, endpoints and more. The attack surface, though not growing and even shrinking in 2024, remains vast and ever-changing, as IT environments are elastic and expand or shrink based on business demands, highlighting the vulnerability of organizations with inflexible security architectures.
Rising attack rate puts all at risk
The likelihood of organizations experiencing a cyberattack remains high, with over 60 percent of Canadian organizations reporting at least one data breach in the past 12 months. Additionally, more than 40 percent of organizations across all segments reported a cloud incident. A sharp rise in denial of service (DoS) infection rate was also reported for smaller organizations, from 34 percent in 2023 to 46 percent in the 2024 study.
ATTACK RATE
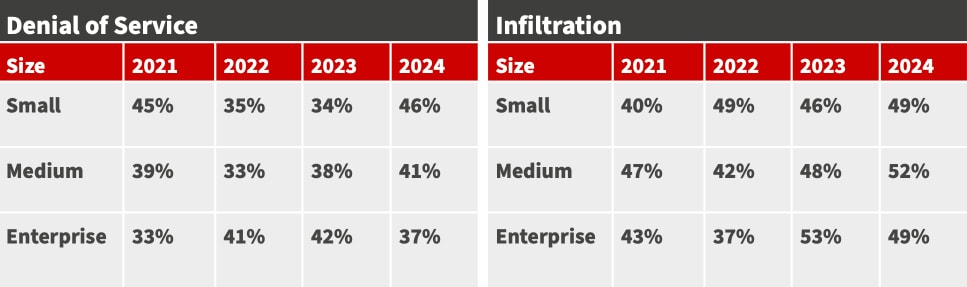
Organizations are facing a significant amount of downtime
Cyberincidents disrupt business operations and put sensitive data at risk – which affects both business reputation and the bottom line. Although downtime remained about the same overall in 2024 compared with the 2023 study, downtime related to breaches and cloud rose by one to three days in the 2024 study, depending on the business size. Canadian firms of all sizes reported total downtime of two weeks or more across most attack categories.
Smaller organizations reported a sharp increase in downtime due to DoS attacks at 18 days, compared with 12 days in the 2023 study. In addition, the average downtime per incident in 2024 increased across industries and business sizes.
Amidst IT cost-cutting, security spending remains a top priority
- Amidst declining IT budgets, the security budget as a percentage of the overall IT budget has increased across industries and organization sizes.
- There is a keen awareness that cyberthreats must be combated to reduce the potential impact on the business.
- Adopting security frameworks can be a helpful starting point toward improving an organization’s overall security posture and maturity.
Cost-cutting is accelerating
Considering the anticipated economic challenges and financial instability in 2024 and beyond, organizations continue to re-evaluate their spending priorities. As a result, Canadian firms are shifting toward more cost-effective technologies, and IT budgets across Canada have declined when compared with the 2023 study.
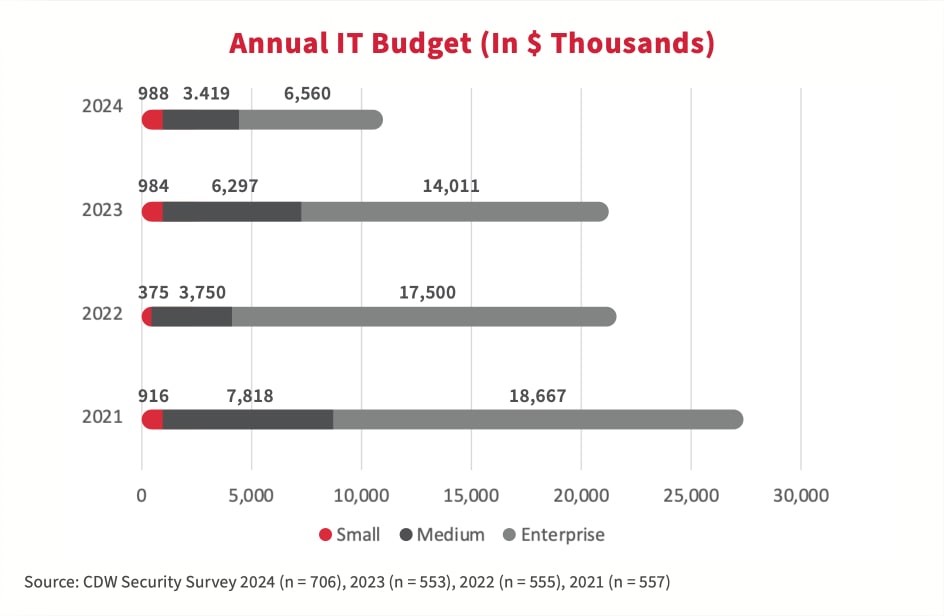
Security spending remains a priority
Despite budget constraints across the board, organizations continue to prioritize cybersecurity investments. According to the 2024 study, security budgets as a proportion of IT budgets have increased year over year for organizations of all sizes and across industries.
Why it is risky to underfund security
Although security spending as a percentage of the IT budget has increased, overall security budgets are down in absolute dollars. Why is this a problem? With less money available to spend on security, organizations may not be able to keep abreast of the latest threats and technologies, making them vulnerable to attacks. Furthermore, as depleted IT security team members contend with the continuous cycle of breach detection, response and recovery, they can experience physical and mental exhaustion, stress and decreased morale.
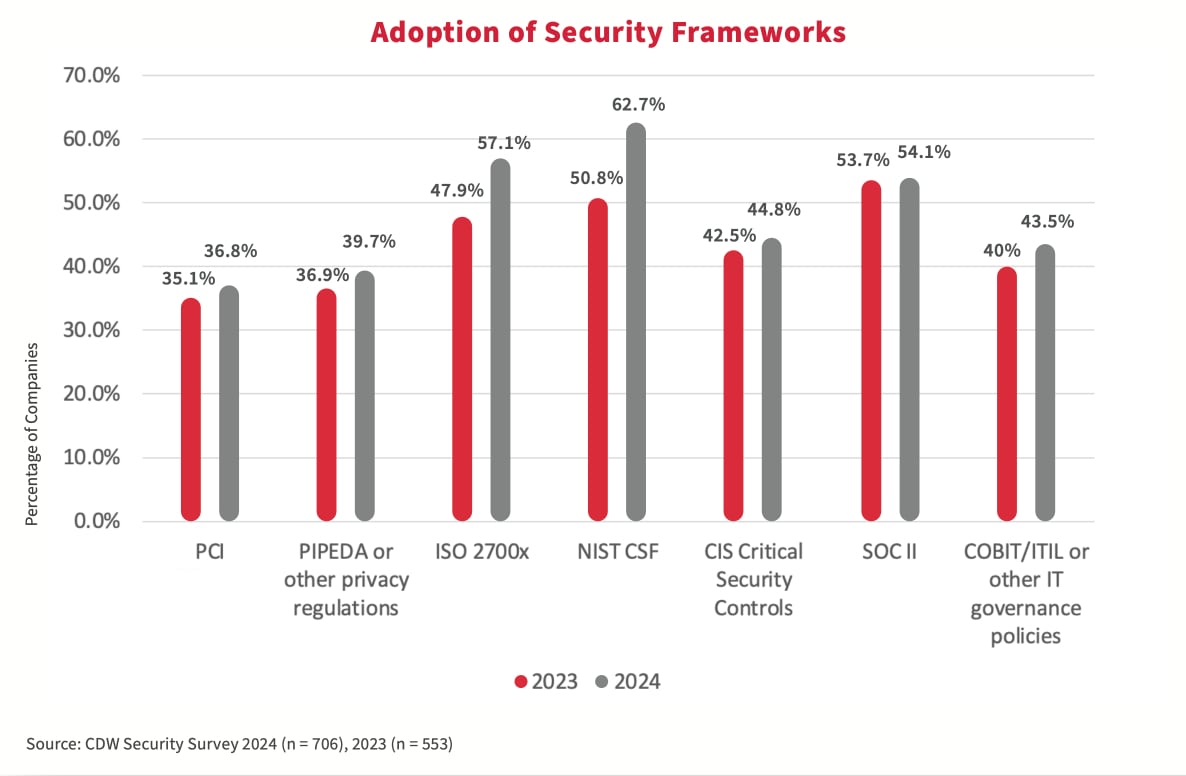
Why security frameworks are needed
The 2024 study showed that an increased adoption of security frameworks is an important first step toward improving maturity. The NIST CSF or other frameworks emphasize a risk-based approach to cybersecurity, helping organizations identify, assess and prioritize cybersecurity risks. By focusing resources on mitigating high-priority risks first, organizations can make more effective use of limited budgets. Also, these frameworks include mechanisms for measuring and evaluating the effectiveness of cybersecurity efforts. By demonstrating measurable results, organizations can justify the value of security spending to stakeholders.
Why zero-trust security must include detection and response
- In the cloud era, zero-trust security has rapidly gained traction.
- While zero-trust access (ZTA) is an essential component of zero-trust security, it should not be the sole focus.
- Threat detection and response are equally important measures to ensure comprehensive security and to meet the long-term objectives of the zero-trust strategy.
Benefits of zero trust
Based on the principle of "never trust, always verify," zero trust ensures that every user, device and network flow is authenticated and authorized before accessing resources. Zero-trust security is particularly beneficial for organizations that have invested in cloud services to support hybrid work, employee mobility and business innovation. Inherent trust is never granted automatically, and scalable architectures can be readily extended to devices and networks, enhancing visibility and control and improving threat detection and response.
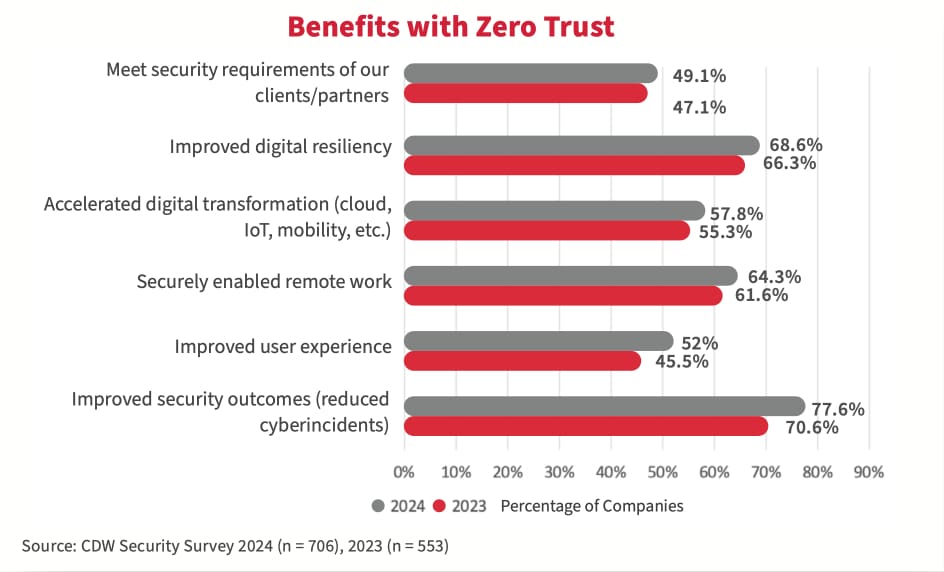
Gaps in security policies supporting zero trust
Zero trust reduces the risk of data breaches by ensuring that only authorized users and devices can access sensitive data. It also improves visibility and control over network traffic, enabling organizations to detect and respond to threats more quickly. However, when we look at adoption of security policies that support a zero-trust strategy, organizations have a long way to go to realize the second benefit.
Gap in technologies supporting threat detection and response
The study showed that there is steady growth in the adoption of many security technologies supporting zero-trust network access, such as identity and access management and multifactor authentication. However, the adoption has declined for threat detection and response technologies (SIEM, XDR, SOAR). Focusing solely on ZTA for threat prevention, without investing in threat detection and response, may lead to a false sense of security. For instance, if an insider threat or a sophisticated phishing attack manages to bypass this barrier, the organization remains vulnerable.
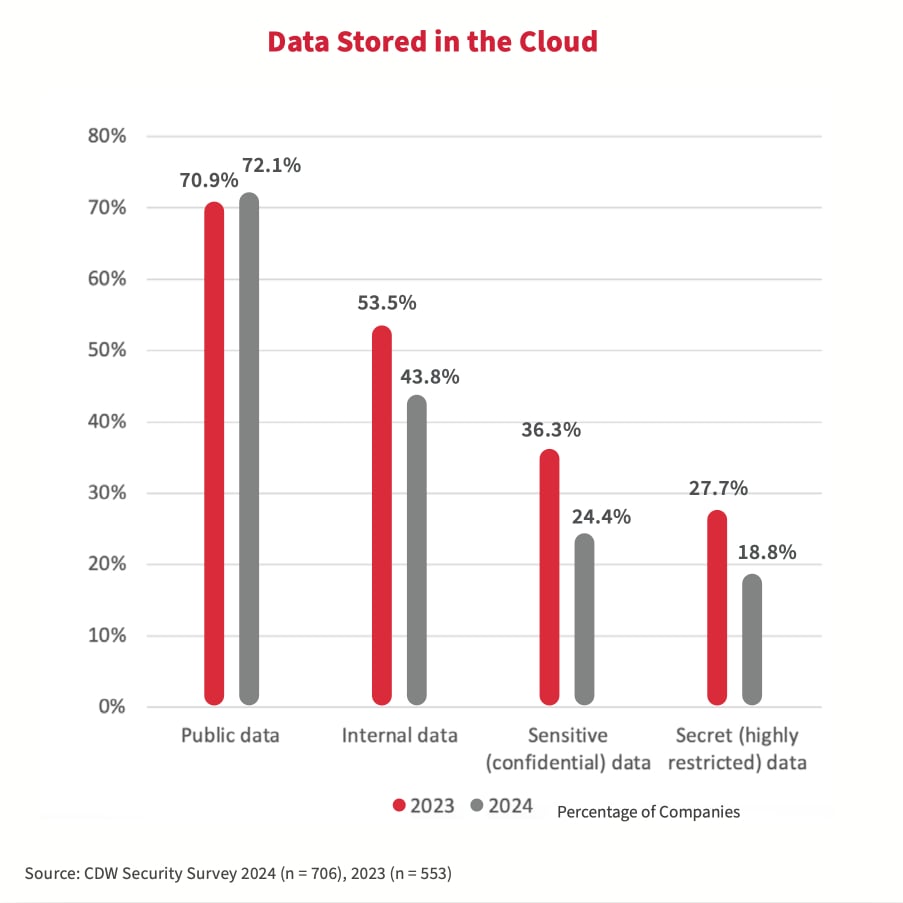
For the last three years, many Canadian organizations have indicated that public cloud environments were the most directly impacted IT component resulting from a cybersecurity attack. As a result, compared with the 2023 study, fewer organizations stored their confidential and secret data in public cloud. The top reason cited by 74 percent of respondents in the 2024 study was their concern about security.
Cybersecurity concerns are hampering cloud adoption
- Canadian organizations view public cloud environments as the most directly impacted component of a cybersecurity incident.
- Point solutions are not the answer.
- An effective approach for addressing gaps in cloud security must consider the entire cloud ecosystem, ensuring that all aspects of the cloud, from its design to its operation, are secure.
The cloud is under attack
Cloud environments have become the most frequently attacked IT components, and the gap between cloud adoption and cloud security investment has manifested into a top cyber risk for many Canadian organizations.
Cyberattacks have eroded confidence in cloud security
Attackers use a variety of methods to target the cloud – everything from “cloud jacking” to cryptojacking to ransomware that targets cloud storage. Consequently, many Canadian organizations believe themselves short-changed on cloud security. According to the 2024 study, 35 percent of respondents do not feel that migrating their IT workloads to public cloud has met their security expectations.
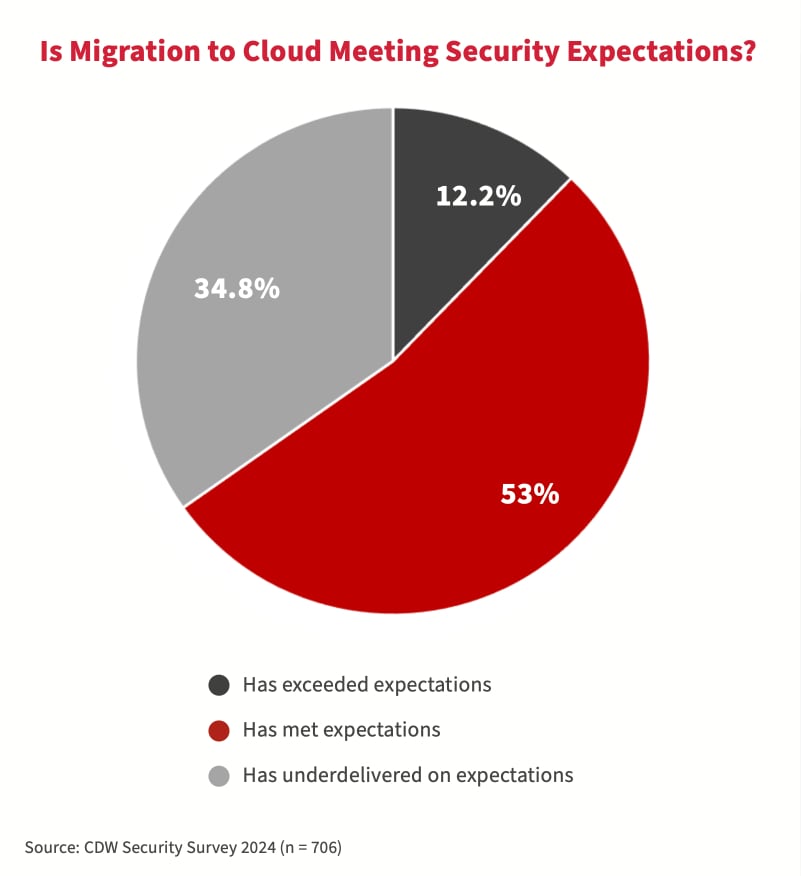
For the last three years, many Canadian organizations have indicated that public cloud environments were the most directly impacted IT component resulting from a cybersecurity attack. As a result, compared with the 2023 study, fewer organizations stored their confidential and secret data in public cloud. The top reason cited by 74 percent of respondents in the 2024 study was their concern about security.
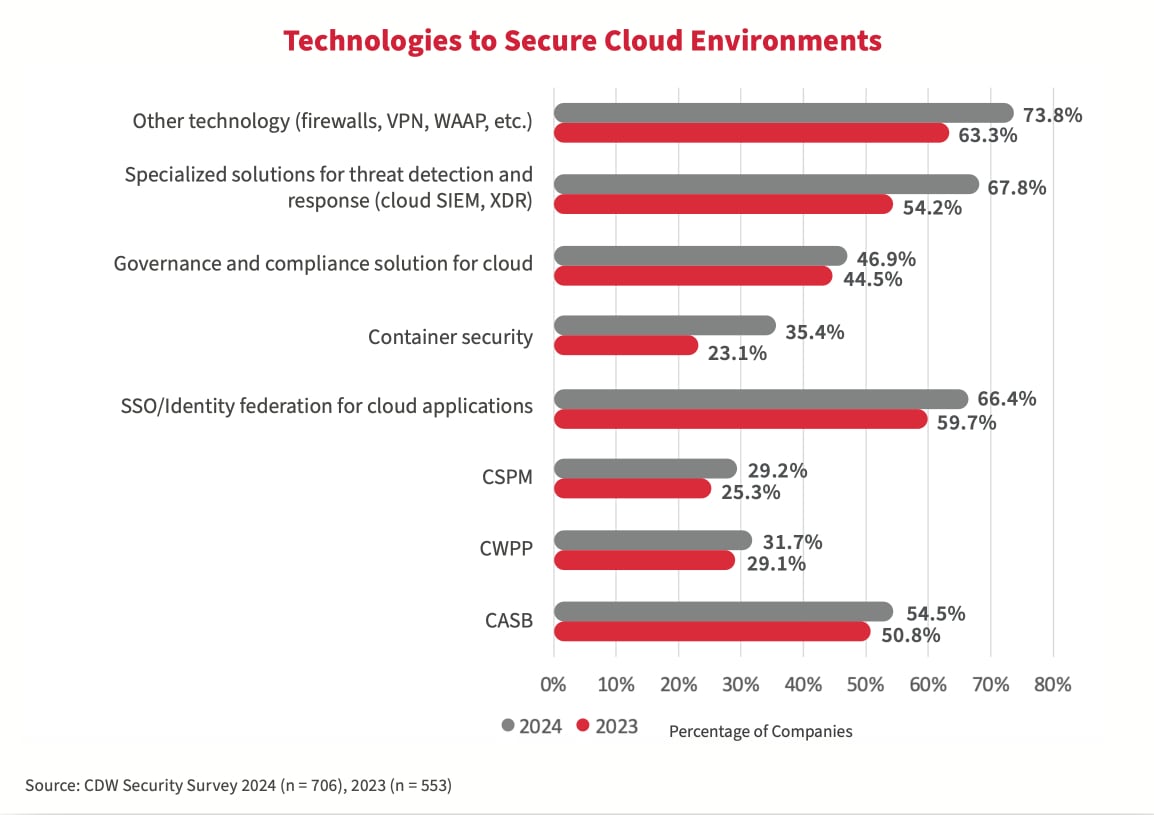
Why investment in technology has not improved security outcomes
Compared with the 2023 study, the adoption of cloud security technologies (point solutions) has grown. However, the 2024 study data does not show a significant reduction in cloud security incidents compared with the previous study. Why not? Point solutions address specific use cases rather than the broader cloud architecture. A more effective strategy considers the entire cloud ecosystem, ensuring that all aspects of the cloud, from its design to its operation, are secure. It also involves continuous monitoring and adaptation to changing threats.
AI and ML are invaluable tools in the modern security landscape
- With its ability to generate human-like text, ChatGPT has demonstrated the power of AI in a tangible, accessible way.
- ChatGPT has demonstrated that AI and machine learning (ML) can be effectively applied to a broad spectrum of use cases, including cybersecurity.
- The success of ChatGPT has accelerated the development of new AI technologies and applications, which has fueled interest in AI for Canadian businesses, creating a positive feedback loop.
A cost-effective approach to cybersecurity
AI and ML are crucial in cybersecurity implementations, thanks to their ability to rapidly analyze vast amounts of data, identify patterns and predict future threats. They can also adapt to evolving IT landscapes and threats, and, despite significant initial investment, can operate with limited resources, making them invaluable in the face of increasing threats, budget shortages and fast-evolving IT landscapes.
The 2024 study showed that AI/ML in IT security is a priority for many Canadian organizations.
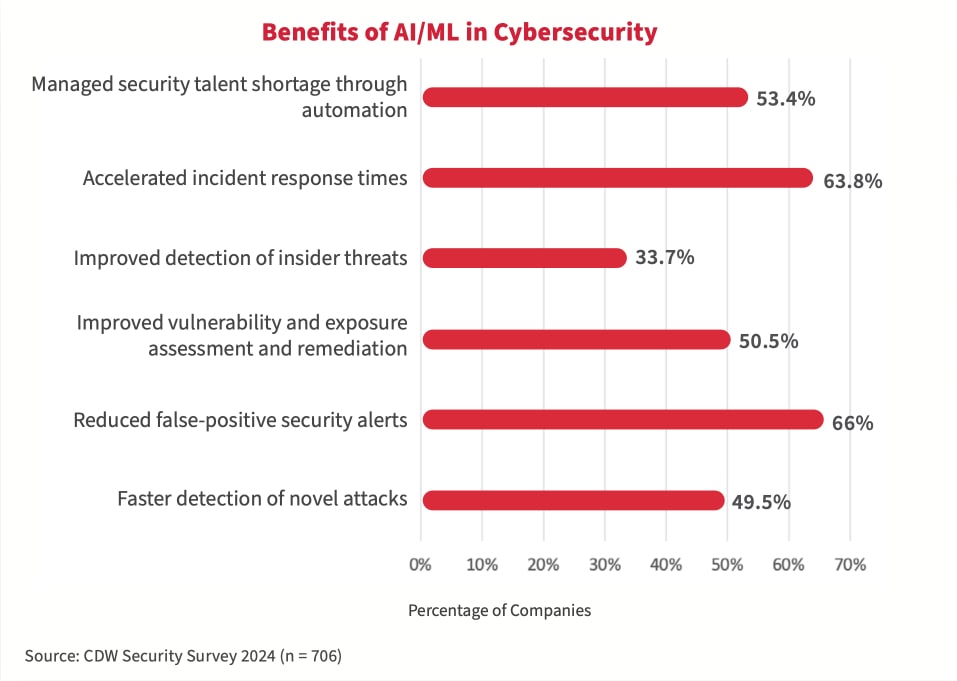
Benefits of AI/ML in cybersecurity
AI/ML can enhance security and streamline operations by significantly reducing false-positive alerts, improving efficiency of security operations and improving incident response times through automated threat detection and response processes. These technologies can also address talent shortages by giving security teams the ability to handle larger workloads without needing to hire additional staff.
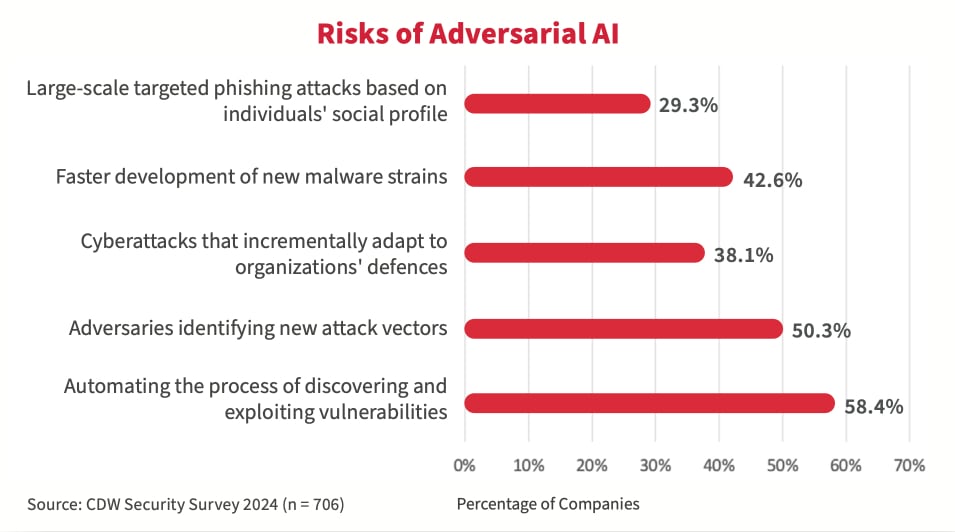
How to combat adversarial AI with AI strategy
- AI and ML are making cybercriminals more formidable than ever before, necessitating robust AI-based defences in cybersecurity.
- Organizations that embrace AI and ML technologies can automate threat detection and response, predict potential threats and manage talent shortages.
- A comprehensive AI strategy helps to ensure that defensive AI is used effectively and responsibly against adversarial AI.
Impact of adversarial AI
The 2024 study showed that Canadian organizations have grave concerns about the risk of AI empowering their adversaries. The top three risks cited include giving cyberattackers the ability to automate the process of discovering and exploiting vulnerabilities (58.4 percent); identify new attack vectors (50.3 percent); and speed up development of new malware strains (42.6 percent).
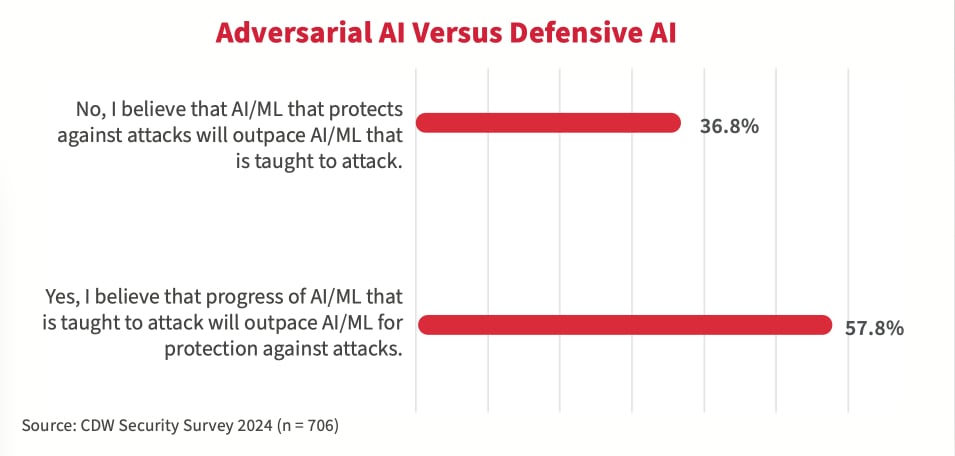
Adversarial AI versus defensive AI
AI can be a double-edged sword in cybersecurity, serving both offensive and defensive roles. While AI could empower the adversaries, AI can also be used by cybersecurity teams to help in real-time threat detection and response, automating the process of identifying and neutralizing threats. AI can also be used to predict potential threats based on historical data and patterns, enabling proactive security measures. However, a majority of survey respondents believe that the development of adversarial AI/ML will outpace the development of defensive AI/ML that protects against attacks.
Why an AI policy is a necessity
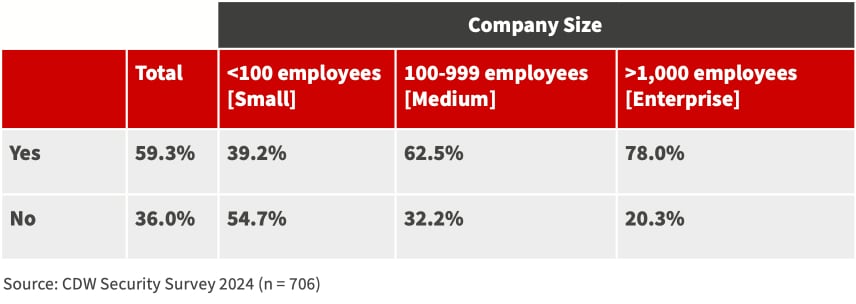
An organization-wide AI policy should outline the organization's stance on AI, including its use, management and ethical considerations. It should also define roles and responsibilities, ensuring that all members of the organization understand their part in implementing and maintaining the AI strategy. According to the 2024 study, 59.3 percent of all Canadian organizations are working toward creating a security policy regarding the use of AI.
AI POLICY IN PLACE
Recommendations and calls to action
I. Prioritize detection and response within a zero-trust strategy
Although ZTA is a pivotal aspect of a holistic zero-trust security strategy, it should not monopolize the focus. Equally crucial are robust threat detection and response mechanisms. Organizations should prioritize all of these areas to fortify their security posture and achieve the long-term goals of the zero-trust strategy. By implementing advanced technologies, fostering a proactive response culture and consistently updating policies, enterprises can ensure comprehensive security and resilient operations in the face of evolving cyberthreats.
II. Strengthen cloud confidence
IT and security leaders must embrace the shared responsibility model, where the cloud service provider (CSP) shoulders the responsibility for the security of the cloud, while the customer is tasked with ensuring security at their end. Security frameworks must be fortified with a risk-based approach backed by stringent access controls. In addition, establishing a comprehensive identity and access management (IAM) system will ensure that only authorized individuals gain access to sensitive data. Cloud monitoring tools form the backbone of effective security measures, while alliances with security experts fill in skills gaps and enhance cloud security proficiency.
III. Create a comprehensive AI strategy for security
Leveraging AI for security involves developing an overarching strategy, establishing policies and governance, investing in AI training, implementing AI security solutions, monitoring and evaluating AI performance. By taking these steps, IT and security leaders can effectively leverage AI within their security, enhancing their ability to detect and respond to security threats.
IV. Implement an effective security framework
While budget constraints may pose challenges, they do not have to prevent organizations from improving their security maturity. Once cyber risks are assessed and documented, they can be effectively managed through a cybersecurity framework such as NIST CSF and ISO 2700x. This provides a structured approach to managing cybersecurity risk by setting up necessary security controls and measures, and helping stakeholders understand the cybersecurity program and its effectiveness. This way, organizations can enhance their security posture and ensure the resilience of their operations.
